
The Simple Checklist to Secure Your Office Wi-Fi Network
Summary: Lock down your router, turn on WPA3 or WPA2, and change all defaults. Separate staff, guest, and smart devices into different networks. Keep firmware…

Summary: Lock down your router, turn on WPA3 or WPA2, and change all defaults. Separate staff, guest, and smart devices into different networks. Keep firmware…
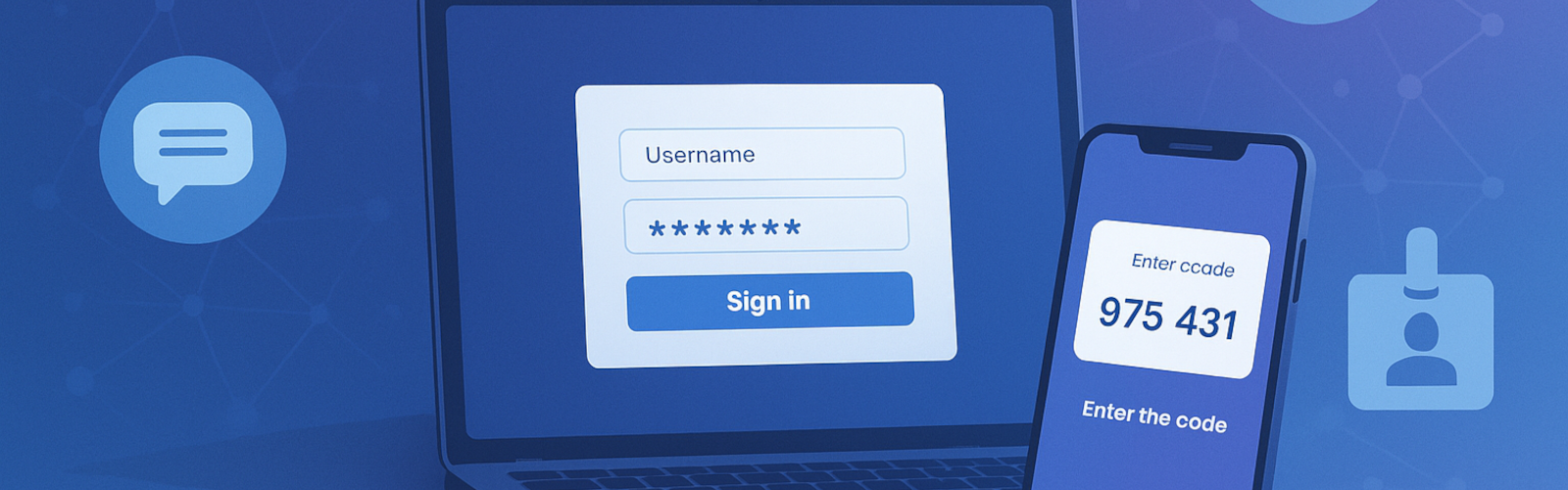
Summary: MFA stops most account takeovers and is now required or strongly recommended by major authorities. Start with email, admin accounts, remote access, finance apps,…

Summary: Encrypt client data in transit and at rest to meet legal duties and reduce breach impact. Use built-in tools like BitLocker and FileVault, and…
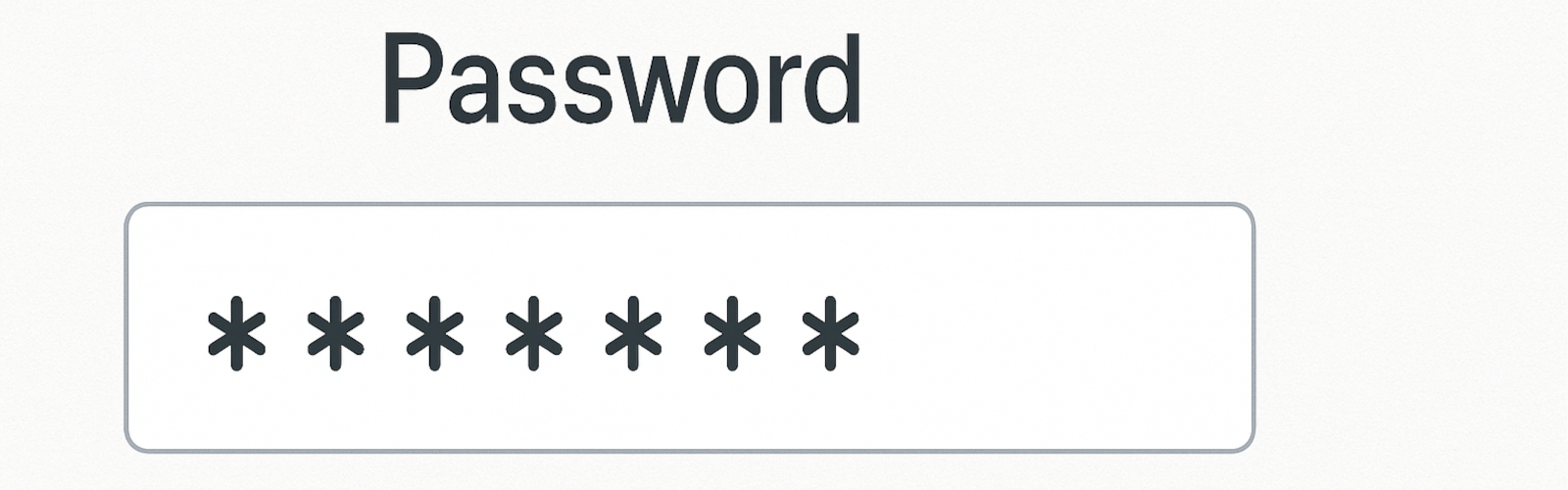
Summary: Long, unique passphrases plus multi-factor authentication stop many attacks Screen new passwords against known breached lists and limit login attempts A managed service provider…

Summary: Set up SPF, DKIM, and DMARC so mailbox providers trust your domain. Follow Gmail, Yahoo, and Outlook sender rules, including one-click unsubscribe for bulk…

Summary: Unsolicited tech support calls are scams. Hang up and do not share info. Pop-ups or emails that tell you to call a number are…

Imagine this: one of your employees calls in to say their company laptop was stolen from their car, hotel room, or coffee shop. Your first…

Email accounts get breached far more often than most businesses admit—and when it happens, the fallout is bigger than “missed messages.” Email is your control…
Email is an important way to communicate—whether for business or personal reasons. But what happens when your email stops working and you’re left offline? The…

If you’ve just clicked on a phishing link, you’re probably starting to worry. Have you just unleashed dangerous malware onto your systems? Is a hacker…

Framing the WISP (Written Information Security Plan) as a strategic risk control Beyond compliance, accountants need a WISP to systematically manage cyber risk, protect client…

In one of the most striking cybersecurity headlines of 2025, a teenager has been arrested over his alleged role in a high-impact cyberattack on MGM…

What happened: a software “poisoning” attack on NPM In early September 2025, security researchers uncovered a coordinated attack on the NPM ecosystem — the central…

Reports in September 2025 indicated that U.S. Immigration and Customs Enforcement (ICE) has reactivated a $2 million contract with Israeli spyware firm Paragon Solutions, granting…

Cloud backups give business owners peace of mind — until they don’t. Many companies assume their data is safe just because they pay for a…
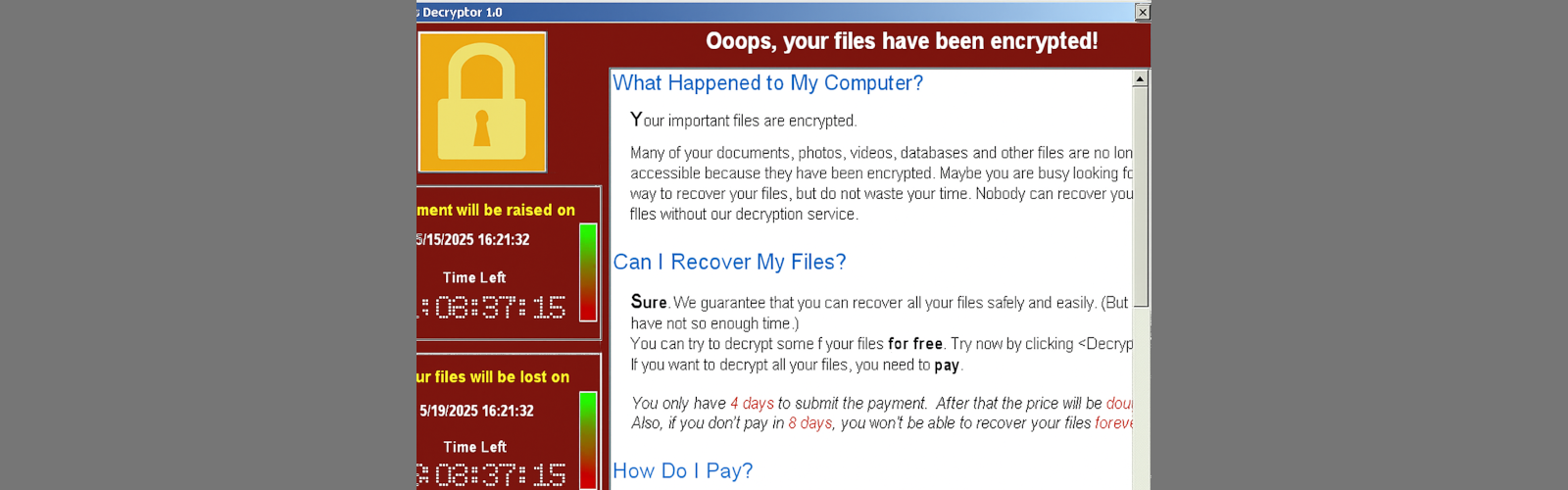
Ransomware remains one of the most pervasive cyber-threats facing businesses today. According to the Unit 42 2025 Incident Response Report, 86% of ransomware incidents had…

What is CVE-2025-53770? CVE-2025-53770 is a critical security vulnerability in Microsoft’s on-premises SharePoint Server family. Trend Micro+3NVD+3Microsoft+3 The flaw allows an attacker to run arbitrary…

Radiology Associates of Richmond (RAR), a prominent medical imaging provider in Virginia, recently confirmed a significant cybersecurity incident that exposed sensitive personal and health information…
Cybersecurity outlet Cybernews announced the exposure of 16 billion login credentials collected from 30 datasets, claiming this was one of the largest credential compilations ever…

In June 2025, Erie Indemnity Company (doing business as Erie Insurance) abruptly disclosed a serious information security incident that knocked core systems offline, impacted customer…